Overview
Configuring Download Settings and Download Studies
mi2b2 client allows users to execute actions configured in the mi2b2 server. However, the "Download to Local Machine" is always available regard of configuration. This document describes how to invoke these actions
Each action may contain several options. For example, the Download action allows users to choose a preferred download location and whether encryption is to be applied. Other actions may require users choose from a list of destinations, for example. All actions and their associated options need to be configured in the server.
Encryption is not demonstrated in the video. To apply encryption, users must supply a key. Encrypted studies have obfuscated versions of file names for the studies, series, and images (as opposed to the unencrypted version that uses the study/series/images ID from DICOM headers ). In addition, an image cannot be viewed (in mi2b2 client or any other DICOM image viewer) without a correct key. The aim of encryption is to add an additional layer of protection on the imaging data.
This document describes the interface by which users can configure these settings. For details about the encryption algorithm, strength, and the process of encrypting downloaded images, please refer the technical note on Encryption.
Video
Requires Flash Player
This video shows the steps in configuring download settings. Learn how to
- Manage space limitations in the repository.
- Download studies to local machine without encryption.
- Cancel active downloads
- Identify what other actions can be performed in Image Repository tab.
- Change/Select download location (or library)
- Load/unload studies to Browser
- View, manipulate images in the Viewer.
Persistence of Download Settings
Download settings is global to the mi2b2 client. That is, if download location is set in the Image Repository tab, the same directory is also the current Library directory (in View Images tab); If a encryption key is set, it is used in all subsequent downloads and reading of image files. The download location (or Library location) is remembered by the client, so the next time users start mi2b2, the same library will be loaded, and all known libraries can be found in the combo box.
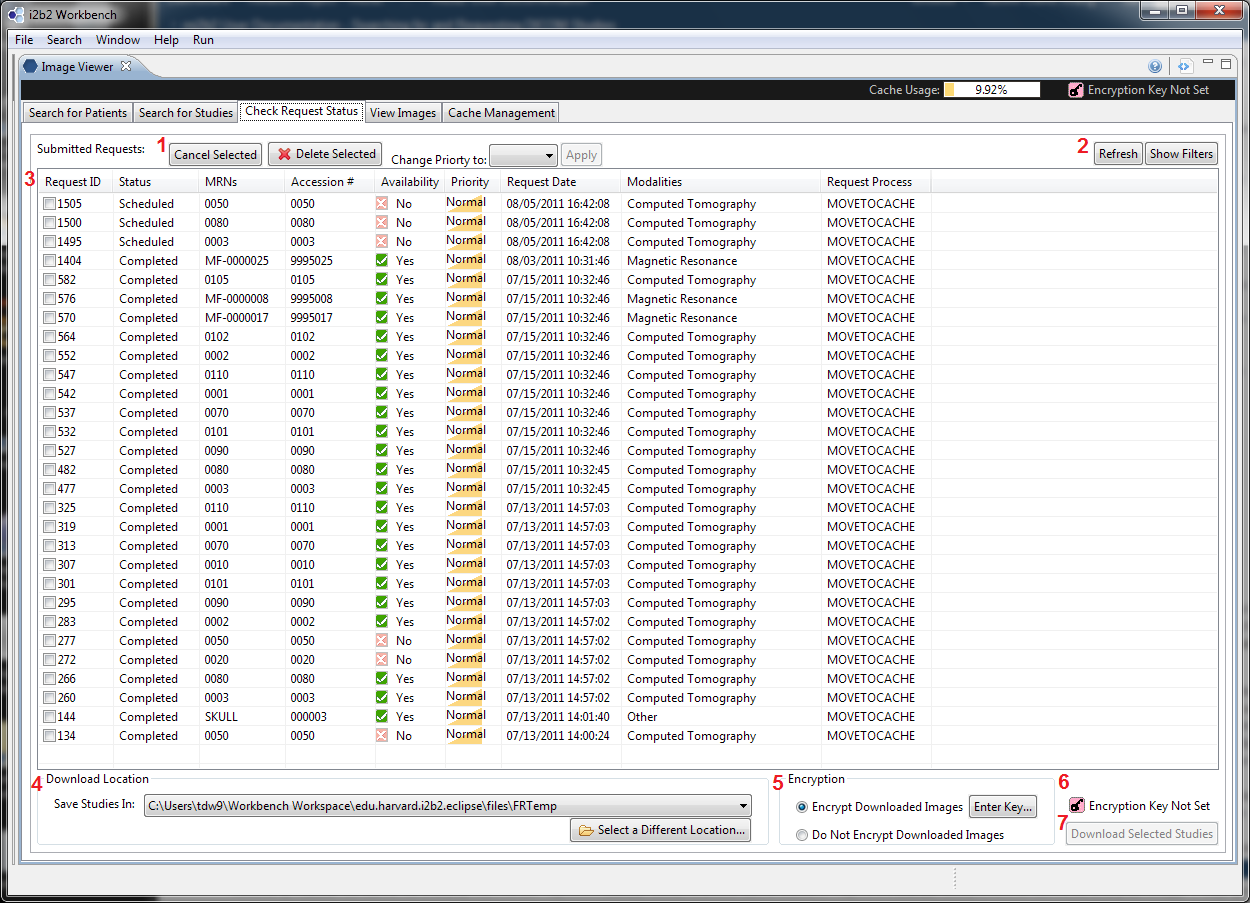
Download From Image Repository
UI Layout
To configure download settings, users would use the UI elements in 4 (configuring download location) and 5 (configuring encryption options).
Once the configuration is complete, the icon (6) becomes green, and the "Download Selected Studies" button (7) will become enabled, allowing users to proceed downloading.
When "Encrypt Downloaded Images" is selected, and "Enter Key..." is pressed in 5, the Key Configuration Dialog will pop up allowing users to select a key (see below) for encryption.
Key Configuration Dialog
Users can select one of
1. (Load key from a file) Users can use a previously generated key file to encrypt subsequent downloads. To browse for a file, use "Browse...". If no such file exists and users want to generate a key, select "Generate Key file...". Once a key file is generated, users will be prompted to save it. Once it is saved, it will be automatically loaded into the mi2b2 client. The same key file can be shared by multiple users to ensure every user on the same project can read these images once downloaded.
2. (Enter a key to generate a key) Users can also enter a key-phrase to generate a key. These keys are generated from a key phrase at least 8 characters long entered directly from the user and concatenated with the user's ID. These keys are meant for single-person use only. Sharing a key phrase with another user will not allow them to generate the same key (because the key generation also takes in user ID).
3. (Use no encryption) Users can also opt not to use encryption. This is not a default choice as users need to consider carefully whether using "No Encryption" is appropriate.
Instructions for each selection are shown in 4, and any warnings are shown in 6. When everything is in order, users can choose "OK" to confirm, or "Cancel" (5).
This Key Configuration Dialog can also be launched any time from the quick link near the top right corner of the mi2b2 client interface:
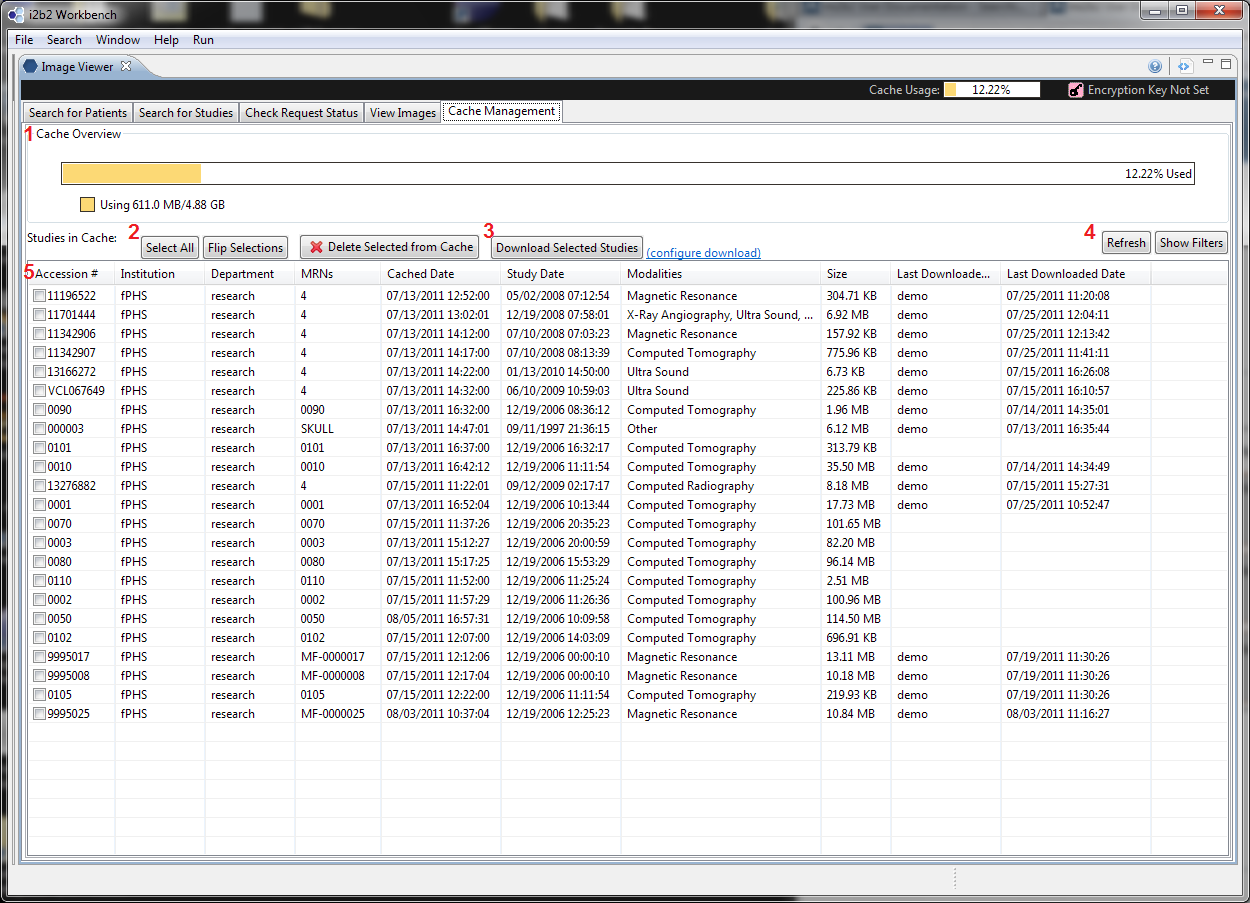
Download From the Cache Management UI
UI Layout
To configure download settings, users would use the link in 3 ("configure download"). The link will launch a dialog that allows users to choose a download location and encryption options. If the configuration is not complete (e.g. encryption is chosen, but no encryption key is given) and when user selects "Download Selected Studies", the same configuration dialog will pop up and prompt users to complete the configuration.
When the "Configure Download" download is selected, download configuration dialog will pop up allowing users to select a download location and a key (see below) for encryption.
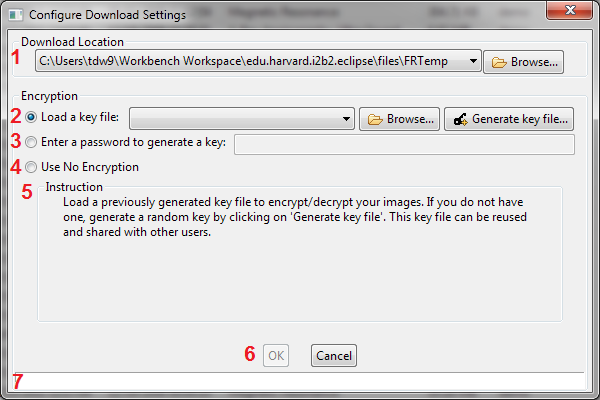
Download Configuration Dialog
The dialog is identical to the key dialog found in the Request Management UI (Tab 3), with the exception that there are widgets to select a download location 1.. Whether users "OK" or "Cancel" this dialog, the download location will be set to the most current value.
Users can select one of
2. (Load a key from a file) Users can use a previously generated key file to encrypt subsequent downloads. To browse for a file, use "Browse...". If no such file exists and users want to generate a key, select "Generate Key file...". Once a key file is generated, users will be prompted to save it. Once it is saved, it will be automatically loaded into the mi2b2 client. The same key file can be shared by multiple users to ensure every user on the same project can read these images once downloaded.
3. (Enter a key to generate a key) Users can also enter a key-phrase to generate a key. These keys are generated from a key phrase at least 8 characters long entered directly from the user and concatenated with the user's ID. These keys are meant for single-person use only. Sharing a key phrase with another user will not allow them to generate the same key (because the key generation also takes in user ID).
4. (Use no encryption) Users can also opt not to use encryption. This is not a default choice as users need to consider carefully whether using "No Encryption" is appropriate.
Instructions for each selection are shown in 5, and any warnings are shown in 7. When everything is in order, users can choose "OK" to confirm, or "Cancel" (6)
Executing Download
After the download settings are properly configured, users can execute download by using "Download Selected Studies" in either the Request Management UI or the Cache Management UI. Users can then view these studies in the Image View UI (Tab 4). See Viewing and Managing Studies for more details.