Overview
Download Studies
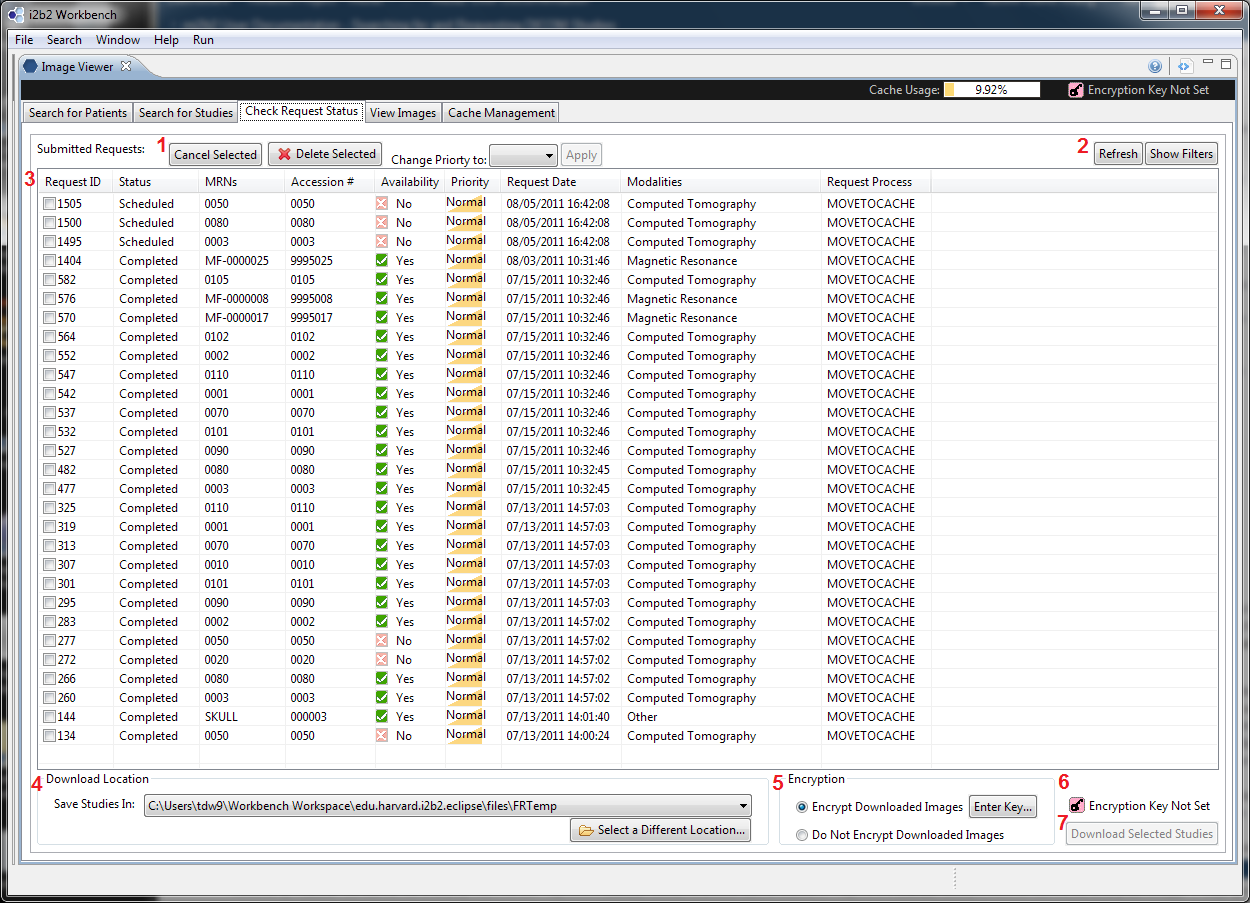
There are two entry points in the UI to initiate a download. The first is in the Request Management UI (Tab 3), the second is in the Cache Management UI (Tab 5).
Each of these entry points require users to configure download settings before download can proceed. Users must set up
- A download location (where the downloaded studies will be stored).
- Encryption options
Encrypted studies have obfuscated versions of file names for the studies, series, and images (as opposed to the unencrypted version that uses the study/series/images ID from DICOM headers ). In addition, an image cannot be viewed (in mi2b2 client or any other DICOM image viewer) without a correct key. The aim of encryption is to add an additional layer of protection on the imaging data.
This document describes the interface by which users can configure these settings.
From the Request Management UI
UI Layout
Configuration UI
When "Encrypt Downloaded Images" is selected, and "Enter Key..." is pressed in 5, a key dialog will pop up allowing users to select a key (see left) for encryption.
Users can select one of
1. (Load a key from a file) Users can use a previously generated key file to encrypt subsequent downloads. To browse for a file, use "Browse...". If no such file exists and users want to generate a key, select "Generate Key file...". Once a key file is generated, users will be prompted to save it. Once it is saved, it will be automatically loaded into the mi2b2 client. The same key file can be shared by multiple users to ensure every user on the same project can read these images once downloaded.
2. (Enter a key to generate a key) Users can also enter a key-phrase to generate a key. These keys are generated from a key phrase at least 8 characters long entered directly from the user and concatenated with the user's ID. These keys are meant for single-person use only. Sharing a key phrase with another user will not allow them to generate the same key (because the key generation also takes in user ID).
3. (Use no encryption) Users can also opt not to use encryption. This is not a default choice as users need to consider carefully whether using "No Encryption" is appropriate.
Instructions are shown in 4, and any warnings are shown in 6. When everything is in order, users can choose "OK" to confirm, or "Cancel" (5)
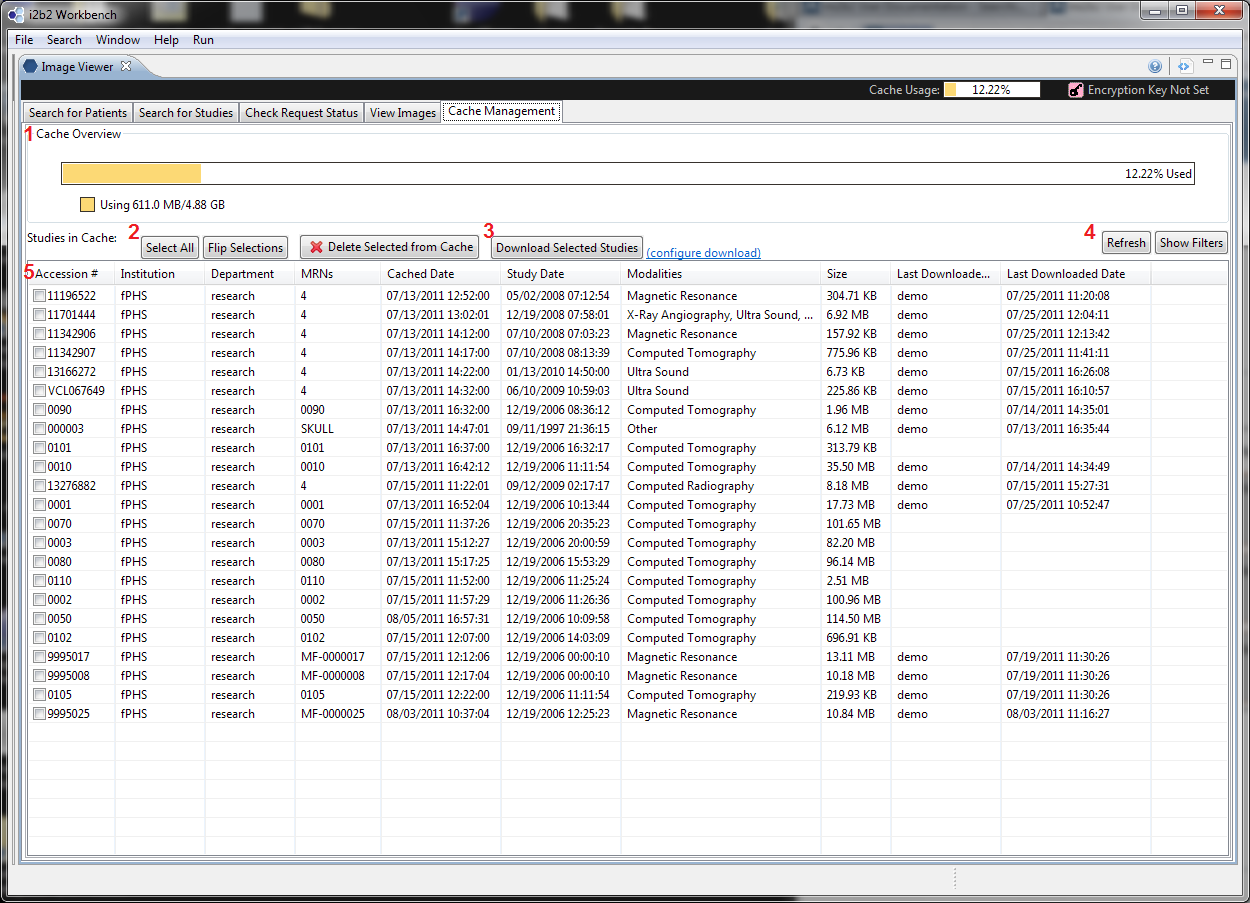
From the Cache Management UI
UI Layout
To configure download settings, users would use the link in 3 ("configure download"). The link will launch a dialog that allows users to choose a download location and encryption options. If the configuration is not complete (e.g. encryption is chosen, but no encryption key is given) and when user selects "Download Selected Studies", the same configuration dialog will pop up and prompt users to complete the configuration.