Page History
...
i2b2 Release 1.7.11
Release Date: February 27 March 6, 2019
Release Summary
Release 1.7.11 contains several new enhancements to the i2b2 kernel, many of which improve the usability of the i2b2 WebClient. We have included a new Identified Data Plan for PHI data and have a license model.
...
| C_TABLE_CD | C_TABLE_NAME | C_PROTECTED_ACCESS | C_HLEVEL | C_FULLNAME | C_NAME | ... | C_ONTOLOGY_PROTECTION |
|---|---|---|---|---|---|---|---|
| i2b2_DEMO | i2b2 | N | 1 | \i2b2\Demographics | Demographics | ... | null |
| i2b2_DIAG | i2b2 | N | 1 | \i2b2\Diagnoses\ | Diagnoses | ... | null |
| i2b2_LABS | i2b2 | N | 1 | \i2b2\Labtests\ | Laboratory Tests | ... | null |
| ... | ... | ... | ... | ... | ... | ... | ... |
| i2b2_PHI | i2b2phi | Y | 1 | \i2b2\PHI\ | PHI Demonstration | ... | DATA_PROT |
New Feature: Workplace Folder drag and drop
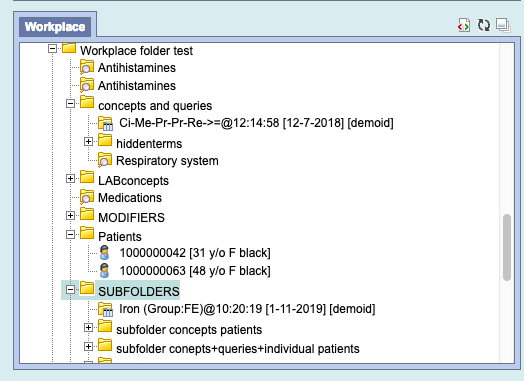
Now you can drag a workplace folder to the query tool, the folder can contain sub folders. All the concepts, previous queries, and individual patients will be displayed in the panel.
Below is the workplace with combination of available items
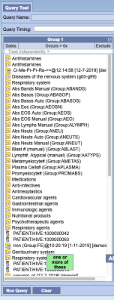
After the drag and drop to the query panel the list of all the items are displayed
New Feature: Individual Patient drag and drop from Previous Query Panel
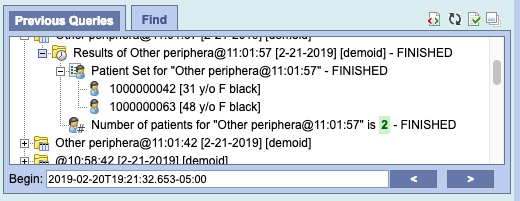
Once a patient set is created, that patient can be dragged and dropped to the Query Tool Panel
Below is a patient set with 2 patients
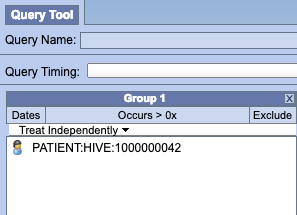
After drag and drop of the individual patient to the query tool panel
New Feature: Previous Queries Upgrade in Web Client
...
The i2b2 software now officially supports WildFly 14. The primary advantages are the faster install/upgrade of i2b2 as a pre-packaged collection (WAR) and managed data source connections/pooling.
New Feature: Inter-CELL SSL Setup
Create server and client certificates (Wildfly 10 & 14)
The keytool utility stores the keys and certificates in a file termed as keystore, a repository of certificates used for identifying a client or a server. Typically, a keystore contains one client or one server's identity, which are protected by using a password.
Create a Self Signed Certificate
You can create a certificate for your server using the following command:
1 | $ keytool -genkey -keyalg RSA -keystore server.keystore -storepass secret -keypass secret -validity 365 -dname "cn=Partners Healtbcare,o=Partners,c=US" |
Now let's copy this keystore into the configuration folder of the application server:
1 | $ cp server.keystore $JBOSS_HOME/standalone/configuration |
Now export the server certificate in a file called server.crt:
1
| $ keytool -exportcert -keystore server.keystore -storepass secret -keypass secret -file server.crt Certificate stored in file <server.crt> |
Now import the cert into the CA for the Java JRE:
1 | $ keytool -import -alias i2b2server -keystore /usr/java/latest/jre/lib/security/cacerts -file server.crt
The password might be changeit |
In /opt/{wildfly} in bin run add-user.sh to create user and select (a) management user
Wildfly 10 Setup
In Wildfly 10 run jboss-cli.sh
Connect to the server
1 | connect |
Start by creating a Security Realm which will contain the keystore and trustore references
1 | /core-service=management/security-realm=SSLRealm:add |
Next, for one-way SSL, set the path to the keystore, along with the keystore path and password:
1 | /core-service=management/security-realm=SSLRealm/server-identity=ssl:adJavathe2d(keystore-path="server.keystore", keystore-relative-to="jboss.server.config.dir", keystore-password="secret") |
Finally, set the value of Undertow's https listener to your Security Realm:
1 | /subsystem=undertow/server=default-server/https-listener=default-https:write-attribute(name=security-realm,value=SSLRealm) |
If the above fails edit the standalone.xml and add right after http-listener
<https-listener name="default-https" security-realm="SSLRealm" socket-binding="https"/>
Wildfly 14 Setup
In Wildfly 14 run jboss.cli.sh
Connect to the server
1 | connect |
Finally, set the value of Undertow's https listener to your Security Realm:
1 | /subsystem=undertow/server=default-server/https-listener=https:write-attribute(name=security-realm,value=ApplicationRealm) |
Both Wildfly 10 and 14
Add the following to the axis2.xml file right after the <transportReceiver name="http"
<transportReceiver name="https"
class="org.apache.axis2.transport.http.AxisServletListener"/>
Change the crc.properties, ontology.properties and workplace.properties files to point to the https://localhost:8443
Database Changes
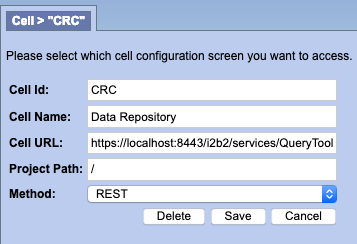
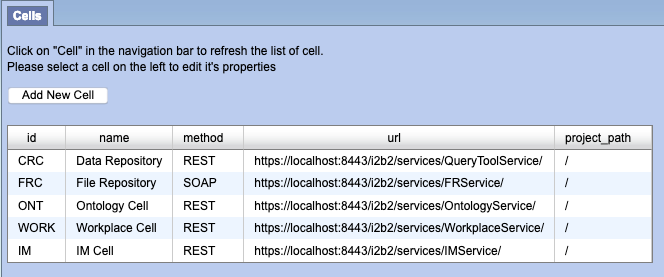
Change all the pm_cell_data within the PM Database to https://localhost:8443
After all the cells have been updated it should look like below.
Webclient Changes
Webclient, if using self-signed cert add the following to the index.php
curl_setopt($proxyRequest, CURLOPT_SSL_VERIFYHOST, 0);
curl_setopt($proxyRequest, CURLOPT_SSL_VERIFYPEER, 0);
Also into the index.php add the new url to the whitelist such as:
$WHITELIST = array(
"http" . (($_SERVER['SERVER_PORT'] == '443') ? 's' : '' ) . "://" . $_SERVER['HTTP_HOST'],
);
Updated: i2b2 License
The i2b2 software is now made available under the terms of the Mozilla Public License (MPL) version 2.0. i2b2 is also distributed under the terms of the Healthcare Disclaimer addendum.
...