Page History
| html-text |
|---|
<a href="https://community.i2b2.org/wiki/download/attachments/16974296/releaseNotes_1710.pdf?api=v2"><img src="https://community.i2b2.org/wiki/download/attachments/851970/printer.png" alt="Printable version of this release note" title="Printable version of this release note" align=right></a> |
| Anchor | ||||
|---|---|---|---|---|
|
| html-text |
|---|
<!DOCTYPE html>
<html>
<head>
<title>i2b2 1.7.10 Release Notes</title>
<meta charset="UTF-8">
<meta name="description" content="The release notes for version 1.7.10 of the i2b2 Software" />
<meta name="keywords" content="i2b2, release, 1.7.10" />
<!-- <link rel="stylesheet" type="text/css" media="all" href="/stylesheets/i2b2-wiki.css" /> -->
</head>
<body>
<h1 class="releaseHeading" id="rel1710">i2b2 Release 1.7.10</h1>
<p class="releaseDate"><b>Release Date:</b> May 14, 2018</p>
</body>
</html> |
| Anchor | ||||
|---|---|---|---|---|
|
Release Summary
Release 1.7.10 contains several new enhancements to the i2b2 kernel, many of which improve the security around signing into the i2b2 Web Client. We have included some Auditing features like logging all successful and attempted logins into the i2b2 Web Client or keeping a log of all the Admin functions performed with the Admin Module.
Highlight of Features
- Log admin and sign on activity
- Lock users out after a specific number of failed login attempts
- Require users to change passwords after a specified interval of time
- Prevent users from using the same password when required to change it.
- Enforce complex password requirements defined by the i2b2 Administrator.
- Custom SQL Breakdowns
- Temporal query made simple
- Single sign-on
- Improve datasource validation
| Anchor | ||||
|---|---|---|---|---|
|
Installation Note
The 1.7.10 Release Notes apply to you if you are upgrading your existing i2b2 system from an earlier version of the i2b2 software.
| Type of install | Where you need to go next |
|---|---|
| Upgrading an existing i2b2 (currently installed at your site) | Please go to the Upgrade Notes section for the details about upgrading your i2b2 software. |
| Upgrading your i2b2 in a SHRINE network | Please read the information in the SHRINE Networks section before proceeding. |
| Installing a new instance of i2b2. (Never installed it before) | We recommend you refer to the i2b2 Installation Guide found on the i2b2 Community Wiki. The install guide will take you through the entire installation process. |
| UI Text Box | ||
|---|---|---|
| ||
If you run into issues or have questions you can reach out to the community by emailing the google group called i2b2 Install Help. |
| Anchor | ||||
|---|---|---|---|---|
|
SHRINE Networks
| UI Text Box | ||||
|---|---|---|---|---|
| ||||
WARNING Release 1.7.10 has not been tested within a SHRINE network. Therefore, i2b2 Release 1.7.10 should not be installed within a SHRINE network. It can be installed independently of SHRINE. However because it has not been tested with SHRINE we can not guarantee all of the new enhancements will continue to work correctly when implemented within a SHRINE environment. |
| Anchor | ||||
|---|---|---|---|---|
|
Upgrade Notes
Information about upgrading i2b2 to version 1.7.10 can be found in this section of the release notes.
| Anchor | ||||
|---|---|---|---|---|
|
i2b2 Components
In release 1.7.10 the following i2b2 components contain changes and therefore need to be updated when upgrading your i2b2 environment.
- i2b2 Database
- i2b2 Server (kernel)
- i2b2 Web Client
| Anchor | ||||
|---|---|---|---|---|
|
Database Drivers
The JDBC drivers were updated to the following versions.
| Driver | New Version |
|---|---|
| ojdbc8.jar | Oracle 1 2.2.0.1 |
| postgresql-42.1.4.jar | postgres 42.1.4 |
| mssql-jdbc-6.2.2.jre8.jar | sql server 6.2.2 |
| Anchor | ||||
|---|---|---|---|---|
|
Upgrade Paths
The i2b2 now provides two options for upgrading your i2b2 server.
- Continue to download the source code provided in the zip file released on www.i2b2.org/software
- Install the precompiled JAR files onto your existing i2b2 server to upgrade it to 1.7.10.
Both are acceptable paths to upgrade your i2b2 server and depending on which you choose will determine where you need to go to obtain the appropriate files. The location of the upgrade files for each component is outlined below.
| Anchor | ||||
|---|---|---|---|---|
|
Upgrade Software
| Description | Where to find it | Requirements |
|---|---|---|
| Upgrade i2b2 database to 1.7.10 | Software page (i2b2 Website) | Download i2b2createdb-1710.zip file under Source Code |
| Upgrade i2b2 Web Client to 1.7.10 | Software page (i2b2 Website) | Download i2b2webclient-1710.zip file under Source Code |
| Upgrade i2b2 Server to 1.7.10 (Source Code) | Software page (i2b2 Website) | Download i2b2core-src-1710.zip file under Source Code |
| Upgrade i2b2 Server to 1.7.10 (JAR files) | Upgrade to Release 1.7.10 from 1.7.09c page (Community Wiki) | See Technical Details section on the i2b2 Upgrades page and upgrade documentation on Upgrade to latest version page. |
| Anchor | ||||
|---|---|---|---|---|
|
Upgrade Documentation
| Documentation | Where to find it | Website |
|---|---|---|
| Database changes included in this release | Database Changes | |
| List of core changes included in this release | Change Summary - i2b2 Kernel (Core Software) | |
| List of Web Client changes included in this release | Change Summary - i2b2 Web Client | |
| Details about the new features | Details about New Features in Release 1.7.10 | |
| Technical details and notes about upgrading the i2b2 server | Upgrade i2b2 page | i2b2 Community Wiki |
| Upgrade Instructions (server) | Upgrade to latest version page (Instructions section) | i2b2 Community Wiki |
| Core documentation - Technical doc for i2b2 cells | i2b2 Documentation zip file (i2b2core-doc-1710.zip) | i2b2 Website/software |
These sections are located within this document. All other documents are external pages either on the community wiki or on the i2b2 Website.
| Anchor | ||||
|---|---|---|---|---|
|
Database Changes
Release 1.7.10 involves a few changes to the i2b2 Database. Some are simple an addition to the sample data that is included in the demo data that is delivered with the software while others are changes to the database structure to support new features that are included in 1.7.10
Crcdata Tables
QT_BREAKDOWN_PATH
- Added new breakdowns for the new SQL Query Breakdown feature
QT_QUERY_RESULT_TYPE
- Added new breakdowns for the new SQL Query Breakdown feature
- Added new column to support roles based access for the new SQL Breakdowns
- New column name = QT_ROLE_CD
Pmdata Tables
PM_USER_LOGIN table
- Remove the primary key
- Added the PM_USER_LOGIN_IDX index
| Anchor | ||||
|---|---|---|---|---|
|
Change Summary - Release 1.7.10
Did you know?
- Changes to the i2b2 server & database are listed under i2b2 Kernel (Core) Software
- Changes to the i2b2 Web Client are listed under i2b2 Web Client Software
- Additional information about the new features can be found in the Feature Details - Release 1.7.10 section located this Change Summary section.
| Anchor | ||||
|---|---|---|---|---|
|
i2b2 Kernel (Core Software)
New Features and Improvements
| Jira | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
|
Bug Fixes
| Jira | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
|
| Anchor | ||||
|---|---|---|---|---|
|
i2b2 Web Client Software
New Features and Improvements
| Jira | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
|
Bug Fixes
| Jira | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
|
| Anchor | ||||
|---|---|---|---|---|
|
Feature Details - Release 1.7.10
Release 1.7.10 has many new features and for the purpose of this document we have grouped them into one of the following four categories:
| Anchor | ||||
|---|---|---|---|---|
|
Auditing improvements
The auditing improvements are part of a larger group of enhancements that are labeled in JIRA as "Security enhancements". There are only two auditing features and both involve keeping an audit trail of information for maintaining security. Right now the audit trail is limited to the i2b2 Admin module and the process of logging into the i2b2 Web Client.
| UI Text Box | ||
|---|---|---|
| ||
The auditing improvements are strictly server and database security enhancements to capture the information for auditing purposes. The audit information is logged in the PM_USER_LOGIN table for both features. Due to different security requirements on who can access this type of database information we have chosen to not include a way for i2b2 users to view or print the audit information from within the i2b2. This decision may be reviewed again for a future release. For now, if a site wants to obtain the logged information they can query their i2b2 database and retrieve the information directly from the PM_USER_LOGIN table. |
| Anchor | ||||
|---|---|---|---|---|
|
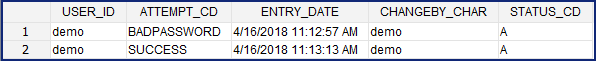
Log number of attempted logins
JIRA Issue: CORE-285
All successful and failed login attempts to sign into the i2b2 Web Client will be logged in the PM_USER_LOGIN table.
Highlights of New Feature
- No additional setup is needed to turn the enhancement on
- Even when a user is locked out the system will log when they attempt to access the system
| Example Box |
|---|
Sample data from PM_USER_LOGIN table
|
| Anchor | ||||
|---|---|---|---|---|
|
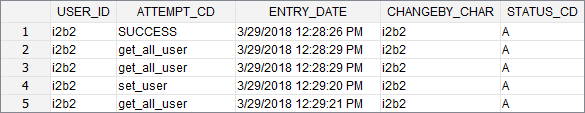
Log Admin Functions
JIRA Issue: CORE-286
Functions performed within the Admin module will be logged within the PM_USER_LOGIN table.
| Example Box |
|---|
EXAMPLEFor the purpose of this documentation, the basic steps an i2b2 Admin rakes to add a new user outlined below: Step 1: Signs into the i2b2 Web Client & select the Administrator project Step 2: Selects Manage Users from the navigation panel Step 3: Clicks on Add User button Step 4: Enters information about the user and clicks on Save. Step 5: Clicks on Manage Users to refresh the list and display the new user in the navigation panel.
As each step was performed, the service and USER_ID was logged in the PM_USER_LOGIN table along with the date & time (server side).
|
| Anchor | ||||
|---|---|---|---|---|
|
Password management improvements
The improvements to managing passwords are the other enhancements that are part of the larger group of "Security enhancements". There are four new features that are designed to help sites improve security of their i2b2 by improving how their user passwords are managed within the i2b2. The site administrators will now have control over requiring users to change passwords, use complex passwords, and lock users out for entering the wrong password too many times.
4 New Features Include
- Account lockout
- Mandatory password change
- Prevent repeat passwords
- Enforce complex passwords
| Anchor | ||||
|---|---|---|---|---|
|
Account Lockout
JIRA Issue: CORE-287
Accounts are locked and users are not able to sign into the i2b2 after a specific number of failed login attempts have been made.
Highlights of New Feature
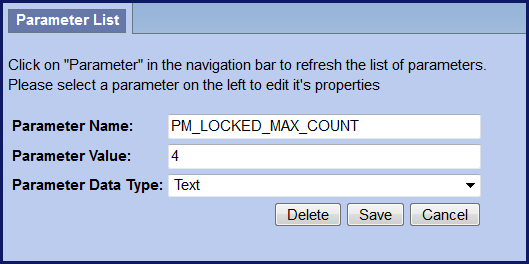
- 2 new global parameters
- PM_LOCKED_MAX_COUNT
- PM_LOCKED_MAX_WAIT_TIME
- Account lockout threshold and wait time is defined by the site Administrator.
- Users are locked-out when the defined number of failed attempts have been reached.
- Once locked
- user receives a lockout message
- user must wait a preset period of time
- Successful login resets the number of failed logins
New Parameters
Two new Global Parameters were created as part of the new lockout feature. These parameters must be defined in the PM_GLOBAL_PARAMS table for users to be locked out after the defined number of failed attempts and number of minutes they must wait before attempting to try again.
| Anchor | ||||
|---|---|---|---|---|
|
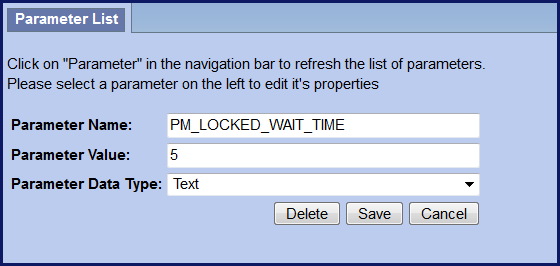
PM_LOCKED_MAX_COUNT Parameter
- Threshold for failed sign-in attempts
- The value is inclusive. i.e. if you enter 4 then the 4th time the user enters the wrong password they will receive the error message and their account will be locked.
| Anchor | ||||
|---|---|---|---|---|
|
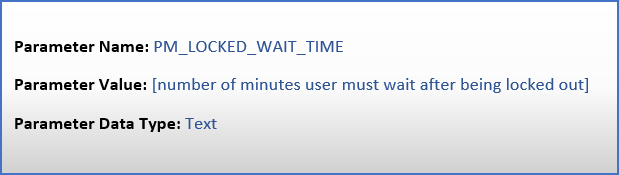
PM_LOCKED_WAIT_TIME Parameter
- Number of minutes an account is locked before a user can sign in again.
| Anchor | ||||
|---|---|---|---|---|
|
Mandatory Password Change
JIRA Issue: CORE-287
Require users to change passwords after a specified interval of time. The i2b2 Administrator controls the number of days allowed before a password must be changed. If a user attempts to sign on after their password has expired, the i2b2 Change Password window will open and the user must change their password before they can sign on. Once the user changes their password, the system will calculate the next expiration date for that user.
Highlights of New Feature
- Require users to change passwords
- i2b2 Admins control how often (interval)
- Change password window will open when password expired
- 2 new parameters; 1 global & 1 user
- The system uses the value in the global parameter to calculate the next expiration date and adds the appropriate user parameter to the table.
Summary of password expiration process
| UI Steps | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ||||||||||||||
|
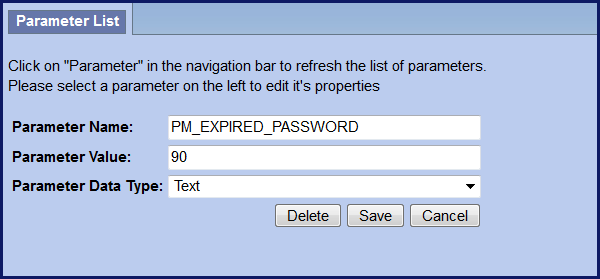
New Parameters
Two new parameters were created as part of the Mandatory password change feature. Both parameters are called PM_EXPIRED_PASSWORD however one is set within PM_GLOBAL_PARAMS and the other within PM_USER_PARAMS. Each parameter has a different function in the password expiration process and is further defined below.
Table: PM_GLOBAL_PARAMS
The new Global Parameter called PM_EXPIRED_PASSWORD must be added to the PM_GLOBAL_PARAMS table to define the password change interval. Once this parameter has been set the mandatory password change feature will be turned on. If this parameter is not added as a global parameter then passwords will never expire.
Highlights of global parameter PM_EXPIRED_PASSWORD
- Global Parameter PM_EXPIRED_PASSWORD
- Turns the feature on
- Defines password change interval
- Affects ALL users
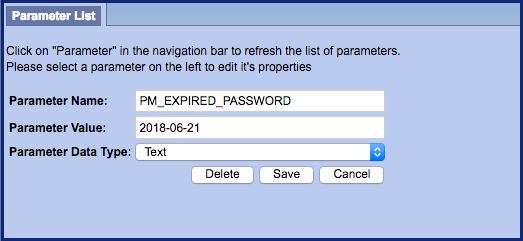
Table: PM_USER_PARAMS
The new user parameter, PM_EXPIRED_PASSWORD, is automatically added to the PM_USER_PARAMS table the first time a user successfully changes their expired password. When they change their password, the system will look to the PM_EXPIRED_PASSWORD parameter in the PM_GLOBAL_PARAMS table to see the change interval defined and then calculate the new expiration date to add to the user parameter.
Highlights of user parameter PM_EXPIRED_PASSWORD
- User Parameter PM_EXPIRED_PASSWORD
- Date password will expire for user
- Added by system when password changed 1st time
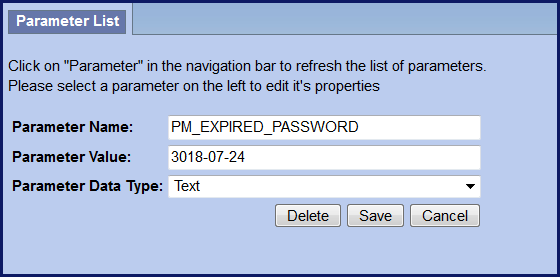
- Can be manually added / edited to a future date for user accounts don't want to expire
| UI Text Box | ||
|---|---|---|
| ||
As soon as you add the PM_EXPIRED_PASSWORD to your PM_GLOBAL_PARAMS table, ALL passwords will expire except the i2b2 AGG_SERVICE_ACCOUNT. To prevent service accounts from expiring you need to add the user parameter as soon as the feature is turned on or even before it. Set the expiration date for a date in the distant future. The following steps outline how to do this.
|
| Anchor | ||||
|---|---|---|---|---|
|
Prevent repeat password
JIRA Issue: CORE-300
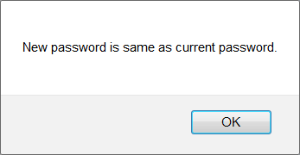
Users are no longer allowed to use their current password as their new password when required to change it.
Highlights of New Feature
- No additional setup is needed
- New password can't be same as current password
- Warning message displayed if user enters same password
| Anchor | ||||
|---|---|---|---|---|
|
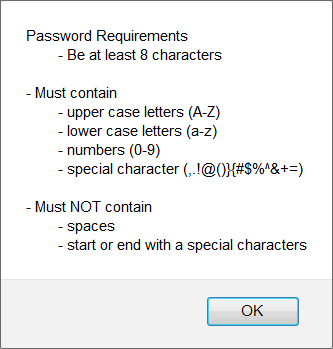
Enforce Complex Passwords
JIRA Issue: CORE-288
Passwords must meet complexity requirements defined by the i2b2 Administrator. The requirements will be enforced when users change their passwords for the Change Password Window. However, when an i2b2 Administrator is setting up a new user in the i2b2 Admin Module the requirements are not required when entering or editing the password in User Management.
Highlights of New Feature
- New global parameter
- i2b2 Administrator defines requirements for complexity
- Requirements are enforced when users change passwords
- User receives Warning message if new password doesn't meet requirements
New parameter
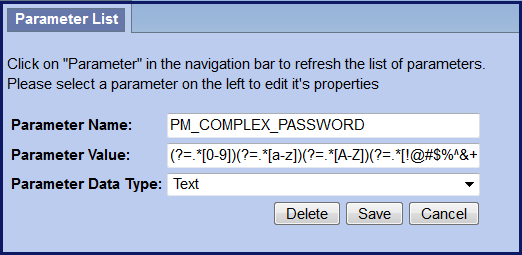
A new Global Parameter was created to support the Enforce Complex Passwords feature. The new parameter defines the complexity requirements for the passwords and once it has been entered into the PM_GLOBAL_PARAMS table the feature will be turned on for all users. This means all users will be required to follow the new requirements the next time they change their password. Again, the only exception is when the password is set by the i2b2 Administrator from within the i2b2 Admin Module.
Global Parameter: PM_COMPLEX_PASSWORD
Table: PM_GLOBAL_PARAMS
Complex Requirement Variables
Setting the parameter value for PM_COMPLEX_PASSWORD
- Each password requirement is defined as an independent variable.
- However, the variables are concatenated into a single string and stored in the VALUE column of the PM_GLOBAL_PARAMS table
The table shown below lists each of the variables and the associated requirement that will be enforced.
| Variables | Requirement |
|---|---|
| (?=.*[0-9]) | Numbers (0-9) |
| (?=.*[a-z]) | Lower case letters (a-z) |
| (?=.*[A-Z]) | Upper case letters (A-Z) |
| (?=.*[!@#$%^&+=]) | Special characters (!@#$%^&+=) |
| (?=\S+$).{8,} | Password is a string and must be 8 characters |
| UI Text Box | ||||
|---|---|---|---|---|
| ||||
The (?=\S+$).{8,} variable is always required when setting the PM_COMPLEX_PASSWORD parameter. The system needs to know that password is a string and the length of password. You do have the option to change the length to be greater or lesser than 8 characters. |
The requirements can be used in any combination. For instance, if the passwords must be 8 characters and contain at least 1 lower case letter and 1 number then the parameter value will be:
(?=.*[0-9])(?=.*[a-z])(?=\S+$).{8,}
If all the requirements in the table were to be used, the following would be entered as the Parameter Value:
(?=.*[0-9])(?=.*[a-z])(?=.*[A-Z])(?=.*[!@#$%^&+=])(?=\S+$).{8,}
| Anchor | ||||
|---|---|---|---|---|
|
Query improvements
The following two new improvements have been made to queries.
- SQL Query Breakdown
- Custom breakdowns based on SQL query
- 4 new breakdowns provided in the demo data as examples
- Temporal Query made simple
- New simple mode available
- Streamlined
| Anchor | ||||
|---|---|---|---|---|
|
SQL Query Breakdowns
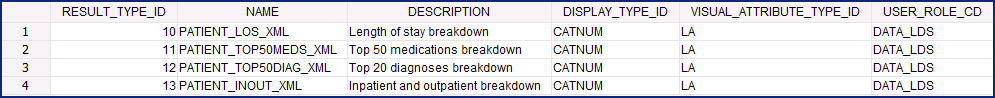
Standard demographic breakdowns have been available in the i2b2 for a long time. For instance, when running a query you can select breakdowns like Gender patient breakdown or Race patient breakdown. Users have also been able to add their own custom breakdowns provided they added the breakdowns in all the appropriate places. In release 1.7.10 we are introducing SQL query breakdowns, which are basically your normal query breakdowns except they have a SQL query built within it. The i2b2 demo data that is delivered with 1.7.10 has been updated to include the following four new SQL query breakdowns
- Length of stay breakdown
- Top 20 medications breakdown
- Top 20 diagnoses breakdown
- Inpatient and outpatient breakdown
| UI Text Box | ||||
|---|---|---|---|---|
| ||||
Now that SQL queries can be run within a breakdown it has become necessary to provide the appropriate level of security to these breakdowns as we would a standard query. Therefore, we have taken the appropriate steps to enable sites to restrict custom breakdowns to a defined role. If the user does not have the appropriate role for the project they are logged into then they will not be able to see the breakdown listed when running a query. The new SQL breakdowns included in 1.7.10 are restricted to the Limited Data Set (DATA_LDS) role. |
- QT_QUERY_RESULT_TYPE table
- QT_BREAKDOWN_PATH table
- CRCApplicationContext.xml file
** New ** Additional Setup Steps for SQL Breakdown
- Add SQL query into the QT_BREAKDOWN_PATH table
- SQL statement goes into the VALUE column
- Add the correct access level into QT_QUERY_RESULT_TYPE table
- The role goes into USER_ROLE_CD column
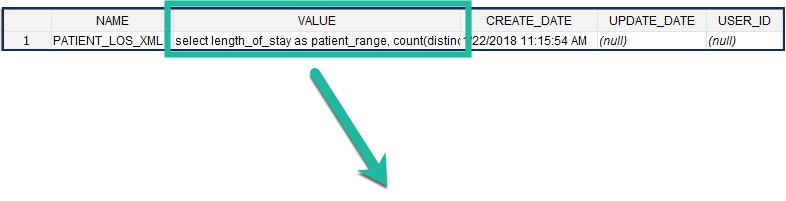
Sample Data: Snapshot of the Length of stay breakdown included in demo data
Define SQL in the QT_BREAKDOWN_PATH table
| Code Block | ||
|---|---|---|
| ||
SELECT length_of_stay AS patient_range, COUNT(DISTINCT a.PATIENT_num) AS patient_count FROM visit_dimension a, DX b WHERE a.patient_num = b.patient_num GROUP BY a.length_of_stay ORDER BY 1 |
Define the appropriate access level in QT_QUERY_RESULT_TYPE table
Running a Query and Viewing Results
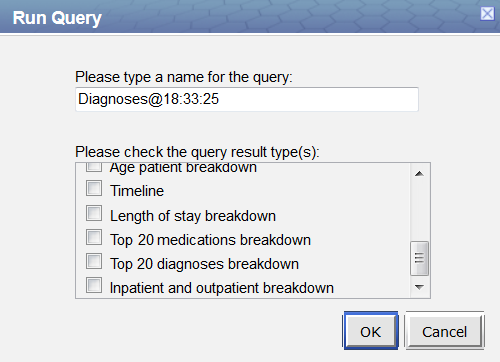
- Provided you have the correct access when you click on the Run button in the Query Tool, the Run Query window will display.
- The list of Result Types, including the SQL breakdowns will display.
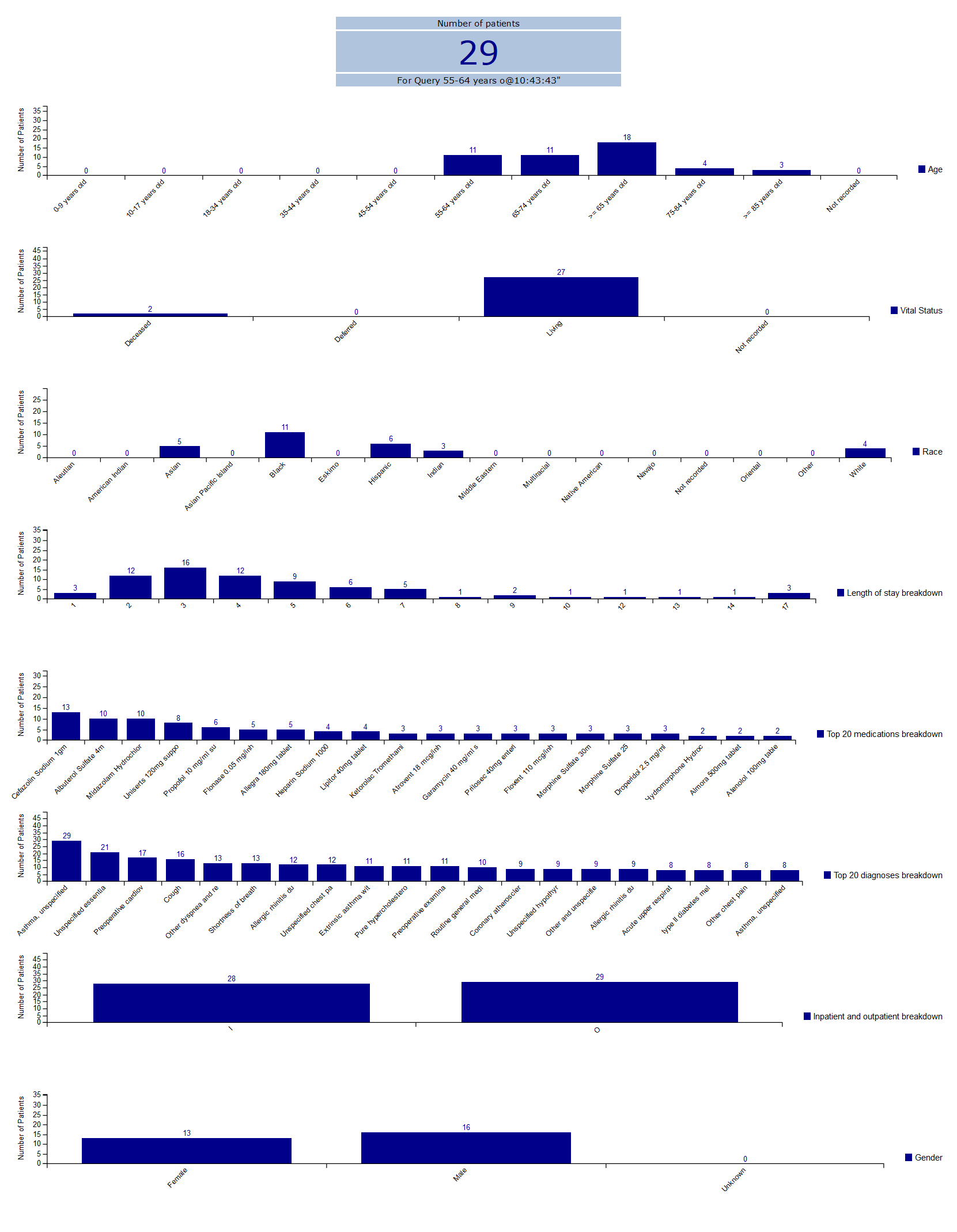
- Check off the different breakdowns the results on the Graph Results tab will display as follows:
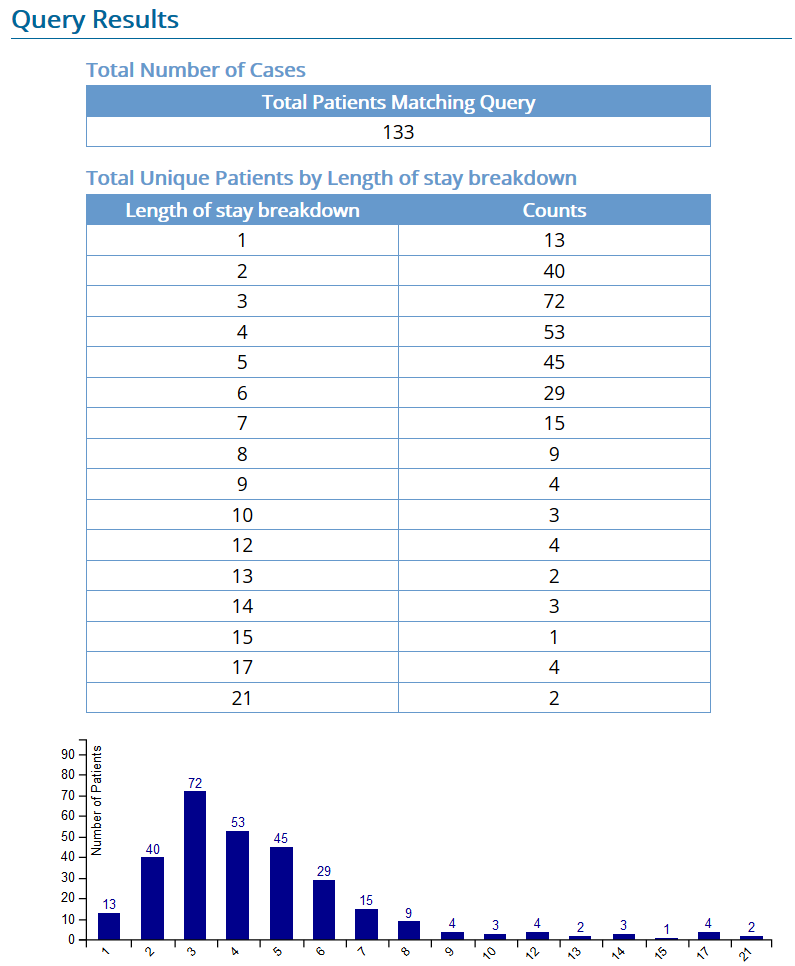
- Click on the Query Report tab to view and print the results of your query.
| Anchor | ||||
|---|---|---|---|---|
|
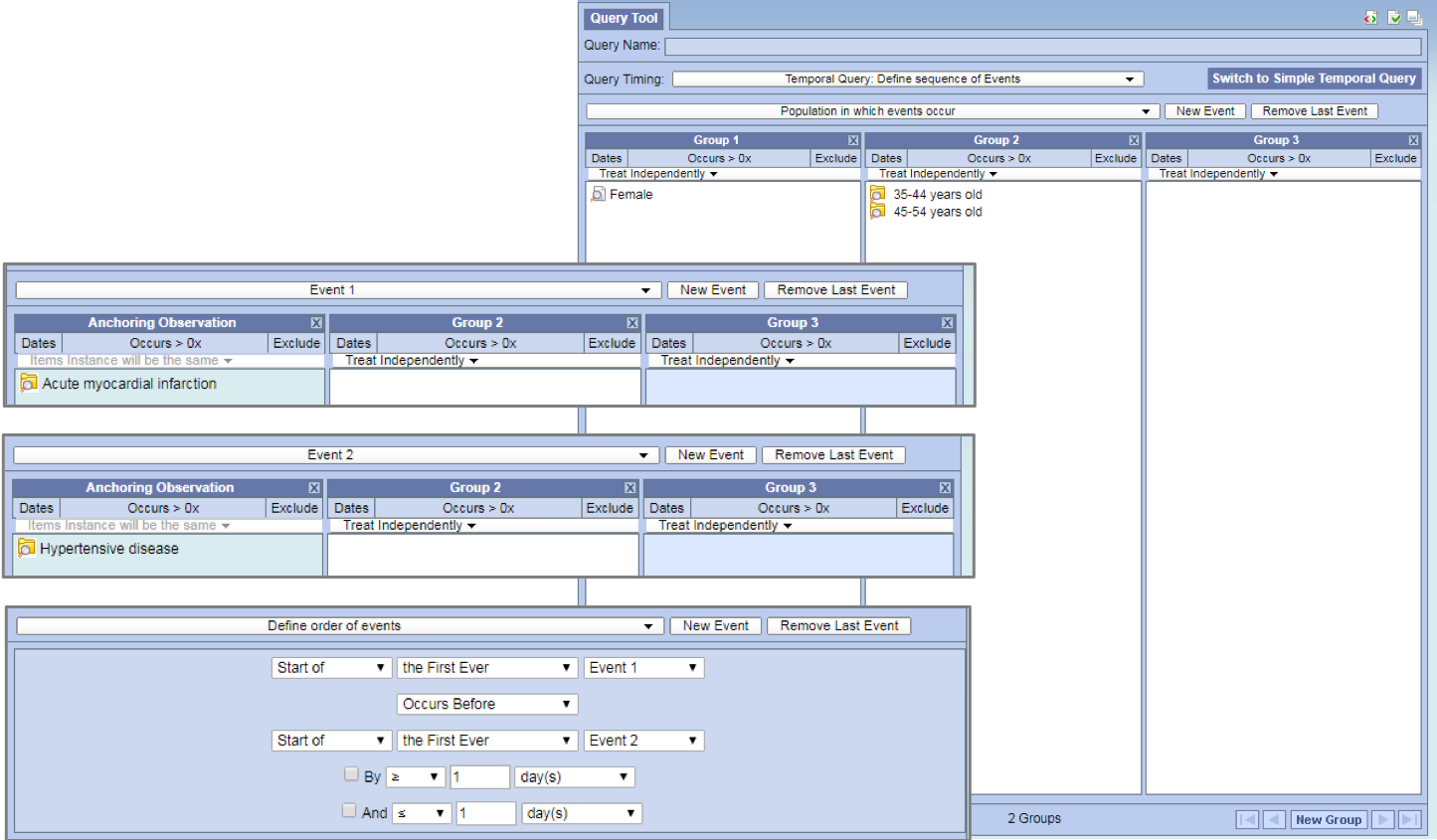
Temporal Query made Simple
Running a temporal query in earlier versions of the i2b2 could be cumbersome and difficult to use. The way the screens were laid out would make it hard to remember population constraints, it was complicated, difficult to learn and hard to comprehend temporality.
In 1.7.10 temporal queries have been made simple by developing a Simple Temporal Query mode. This new mode has streamlined features; displays ordering of events and population constraint on same page.
Simple vs Advanced Mode
Simple mode does not support the following features
- Non-linear temporal sequences
- Multiple Panels
- Number Restrictions
Highlights of New Simple Temporal Query mode
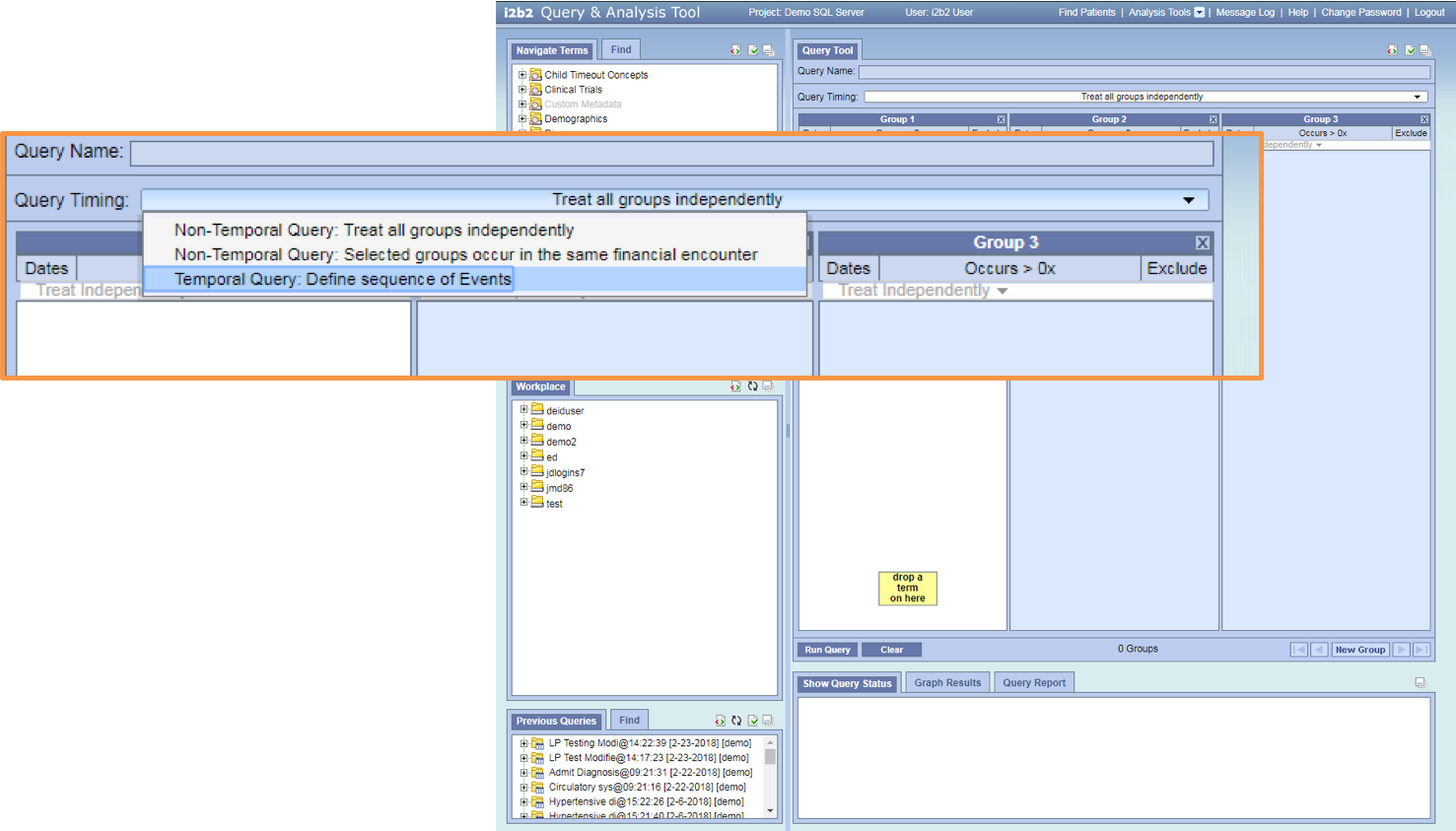
Query Timing list has been updated
- Non-Temporal Query: Treat all groups independently
- Non-Temporal Query: Selected groups occur in the same financial encounter
- Temporal Query: Define sequence of Events
Tutorial Available
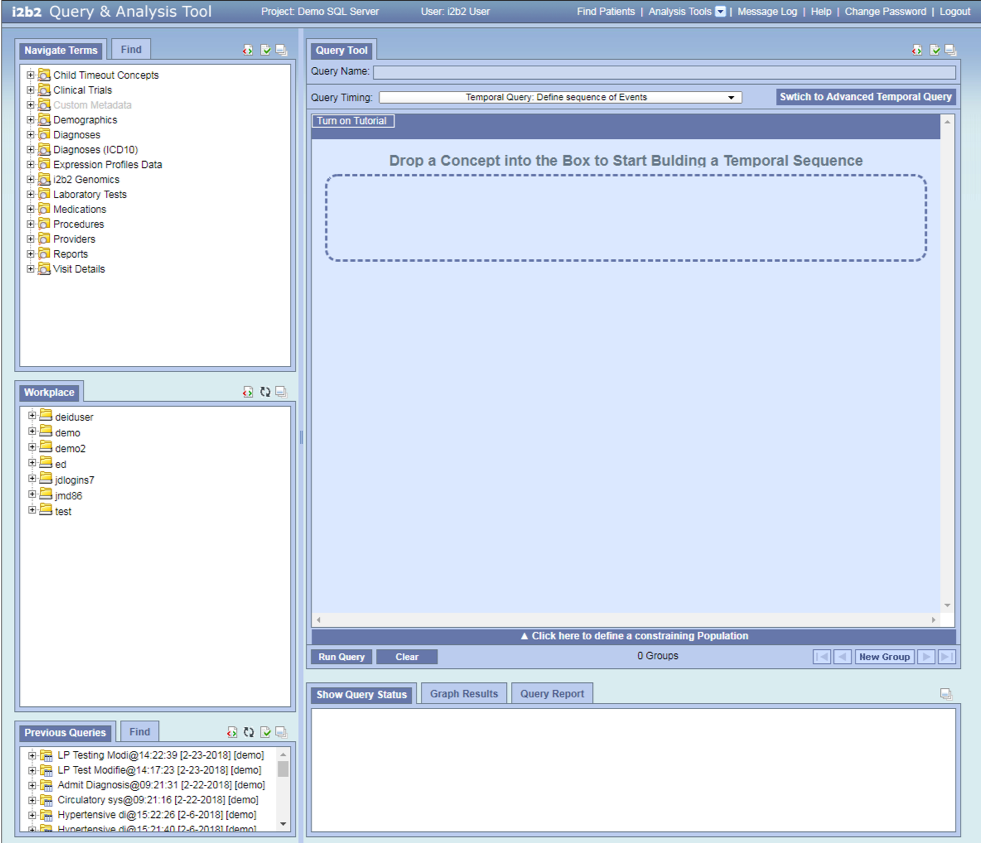
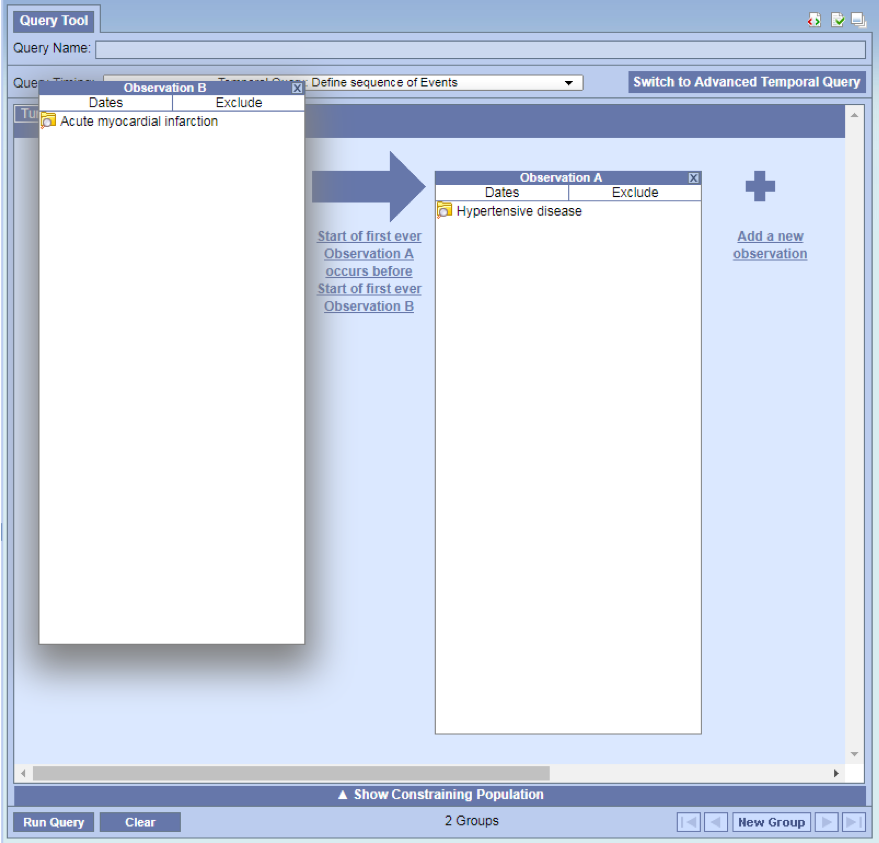
- As soon as you select Temporal Query: Define sequence of Events the simple temporal query mode will display.
- At this point you can either start the Tutorial or begin your query by dragging over an observation.
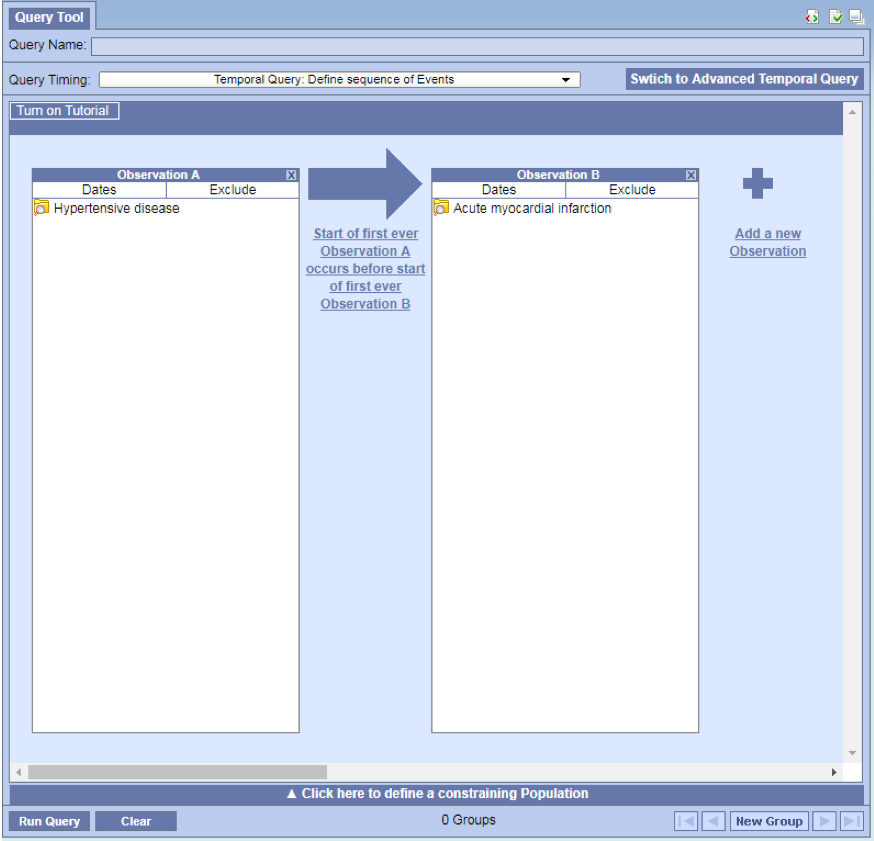
All events are on the same page page
- Add Hypertension into Observation A and Acute Myocardial Infarction into Observation B.
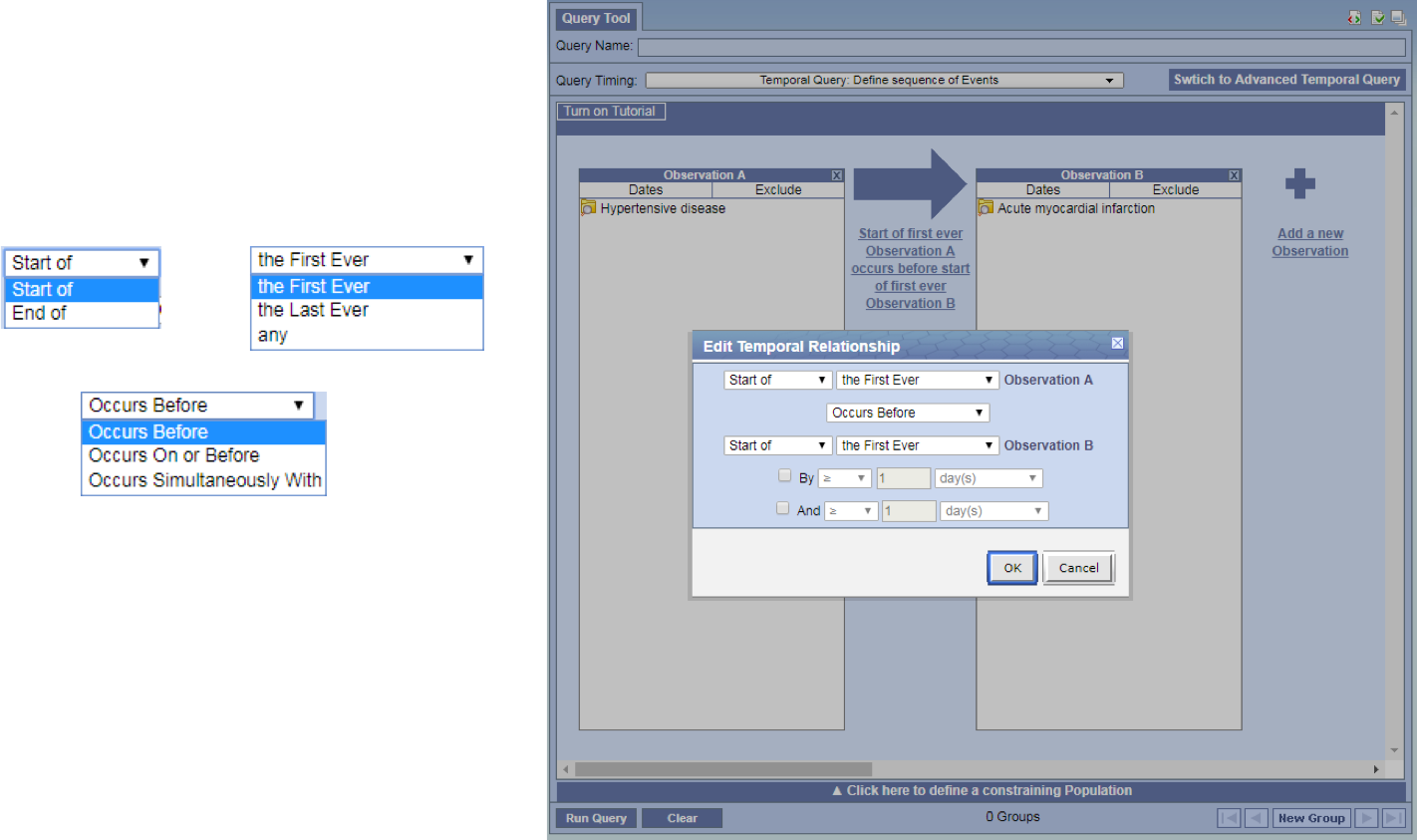
Relationship Editor
- Can edit the relationships without leaving the page.
- Simply click on the text in between the two observations
- The Temporal Relationship window will open with the observations visible behind it
Easily Change Order of Observations
- Swapping position of Observations by dragging the panel
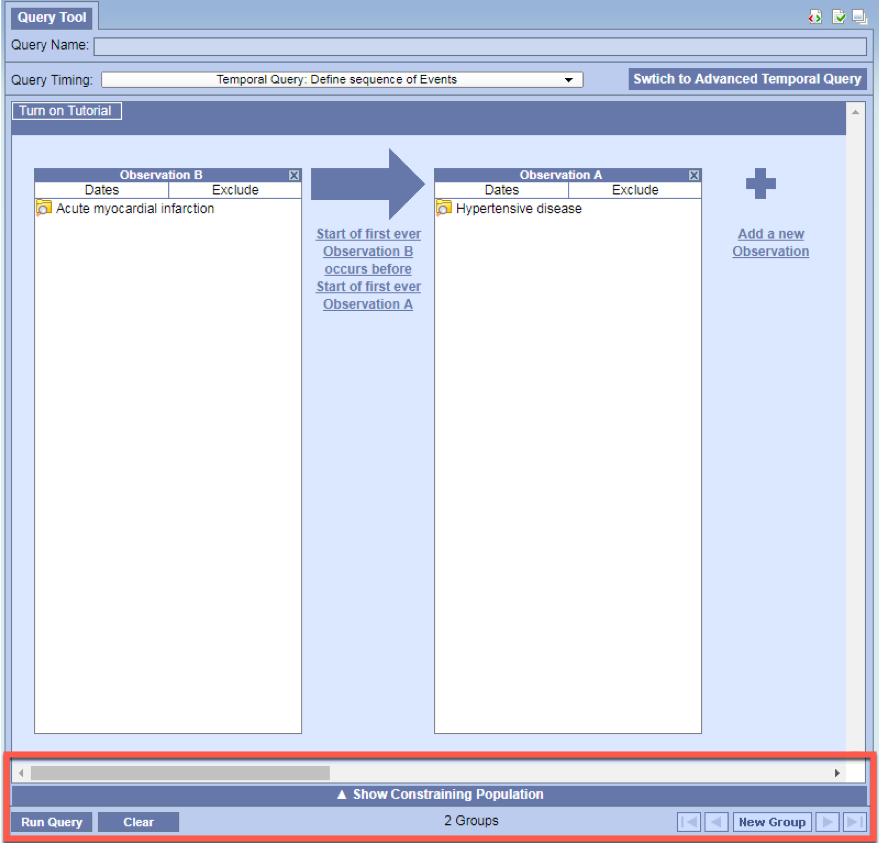
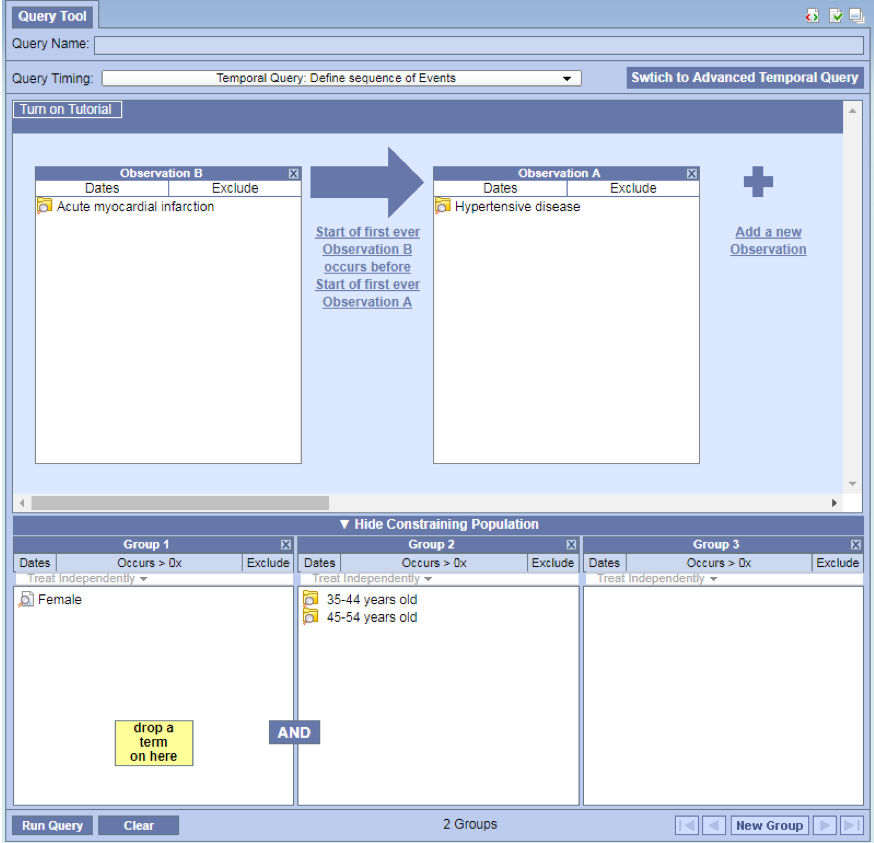
Adding population constraints (optional)
- Can add population constraints without leaving the page.
- Simply click on Show Constraining Population located at the bottom of the view
- The standard 3 panel query view will open on the bottom half where you can add your patient sets.
Switching to advanced mode
- Click on Switch to Advanced Temporal Query to change your mode and query into the old temporal query.
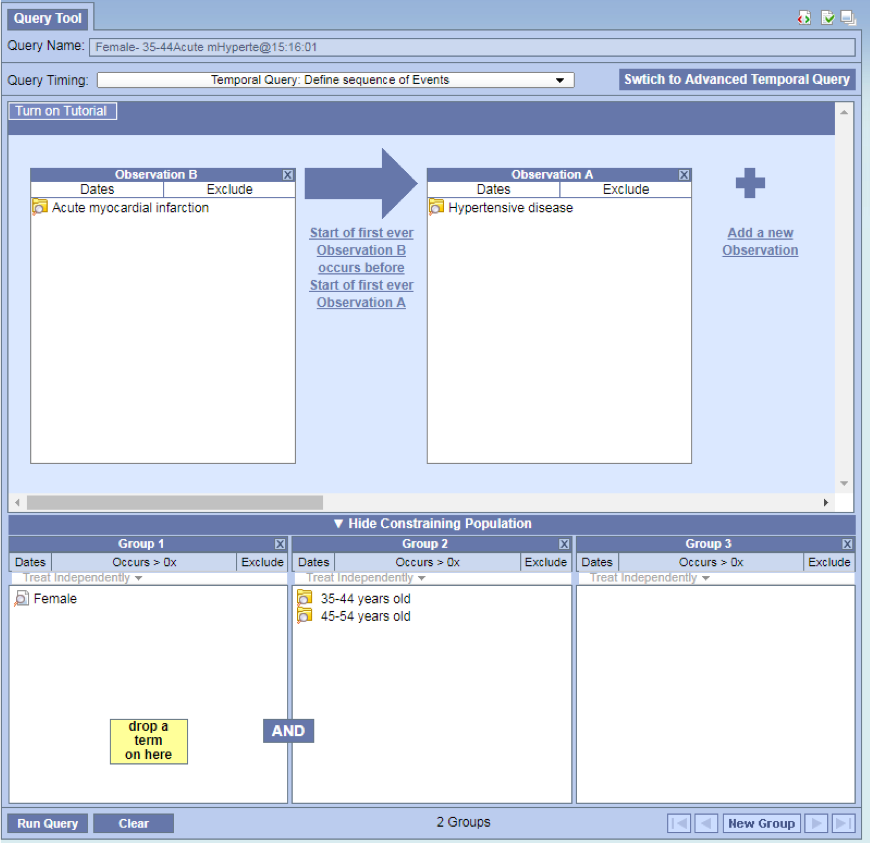
Preserving query between switches
- Queries will be preserved when switching between simple and advanced. The only exception is when a query doesn't meet the simple criteria (i.e. multiple panels, non-linear temporal sequences, number restrictions)
| Anchor | ||||
|---|---|---|---|---|
|
Miscellaneous improvements
| Anchor | ||||
|---|---|---|---|---|
|
Single sign-on location for Web Client and Admin Module
JIRA Issue: WEBCLIENT-226
The i2b2 Admin module no longer needs to be setup on the i2b2 server and results in the following benefits.
- i2b2 Administrators will log in from the same location as the i2b2 Web Client.
- Easier installation and maintenance. Will only install the i2b2 Web Client.
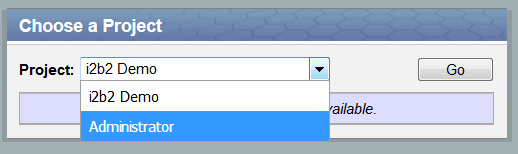
To sign into the i2b2 Admin module, Administrators will go to the same location as their i2b2 Web Client and enter their login credentials. Provided their user is setup as an Admin they will be able to select "Administrator" from the list of projects in the project dialog. The Administrator project will launch the Admin module.
| Anchor | ||||
|---|---|---|---|---|
|
Improve datasource validations
JIRA Issue: CORE-129
On certain occasions a database connection in a pool would go bad and the i2b2 would continue to use the connection which would cause errors in the i2b2. To resolve this problem database connections will now be validated and checked that the connection is valid. If a connection in the pool goes bad the i2b2 will not continue using it.
| Code Block | ||||||
|---|---|---|---|---|---|---|
| ||||||
<validation>
<validate-on-match>true</validate-on-match>
<check-valid-connection-sql>SELECT 1 FROM DUAL</check-valid-connection-sql>
<use-fast-fail>true</use-fast-fail>
</validation> |
| Include Page | ||||
|---|---|---|---|---|
|